Abstract
It was found that Ivanti Workspace Control allows a local (unprivileged) attacker to run arbitrary commands with Administrator privileges. This issue can be exploited by spawning a new Composer process, injecting a malicious thread in this process. This thread connects to a Named Pipe and sends an instruction to a service to launch an attacker-defined application with elevated privileges.
See also
CVE-2018-15592 DOC-69692 - A locally authenticated user with low privileges can run processes with elevated privileges by leveraging an unspecified attack vector
Tested versions
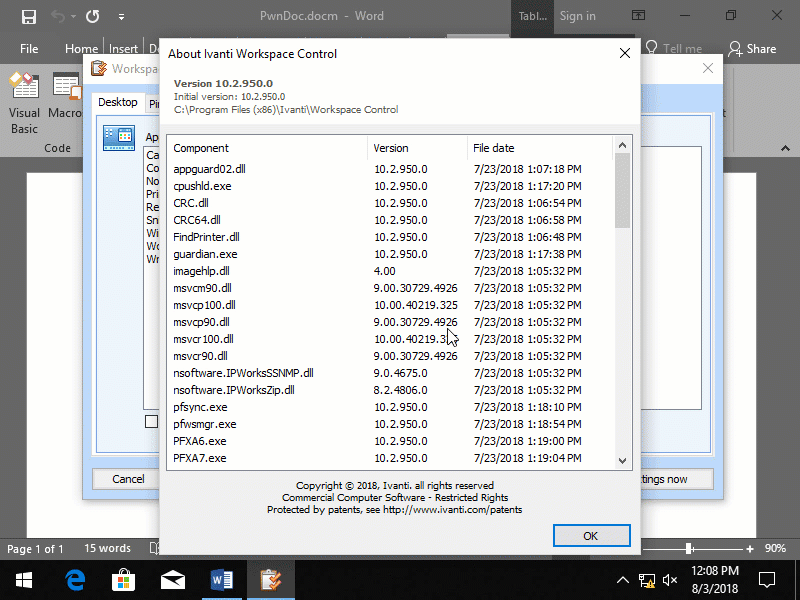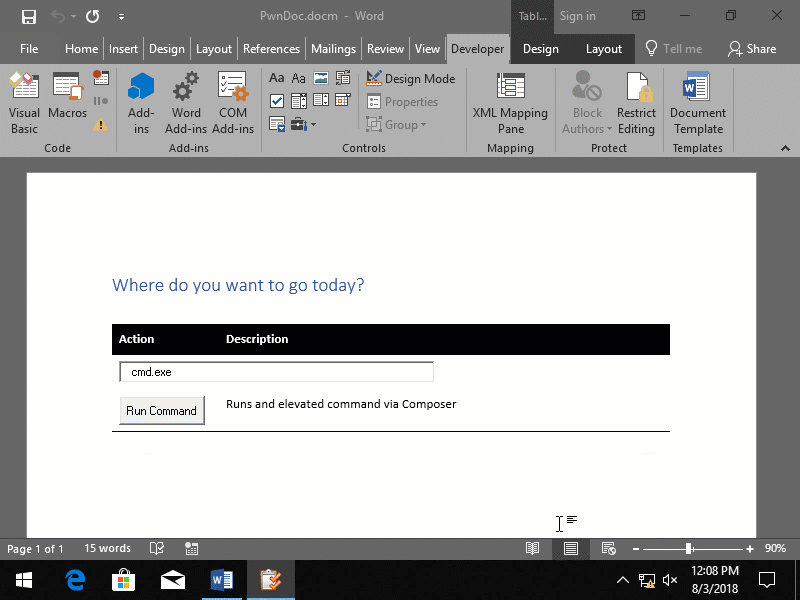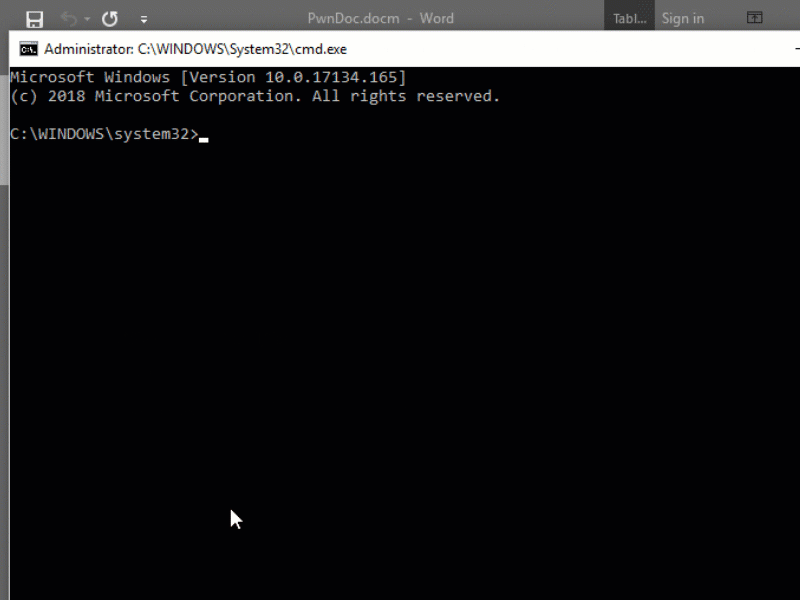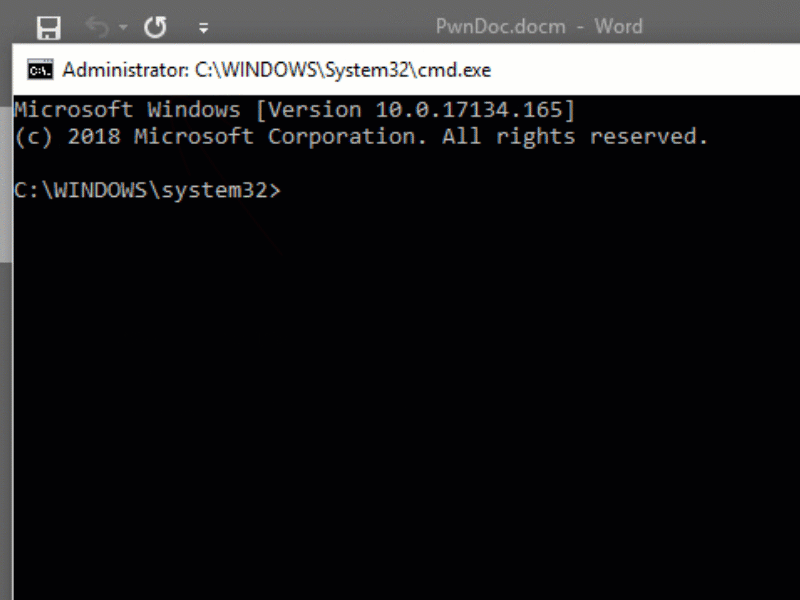
This issue was successfully verified on Ivanti Workspace Control version 10.2.700.1 & 10.2.950.0.
Fix
This issue was resolved in Ivanti Workspace Control version 10.3.10.0.
Introduction
Ivanti Workspace Control (formerly known as RES ONE Workspace) is a User Environment Management solution. Workspace Control contains a feature named Dynamic Privileges that provides the possibility to add or remove Administrator privileges to a process. This is a powerful feature that allows a low privileged user to run an application with Administrator privileges. It was found that this feature can be abused by a local attacker to run any application with Administrator privileges.
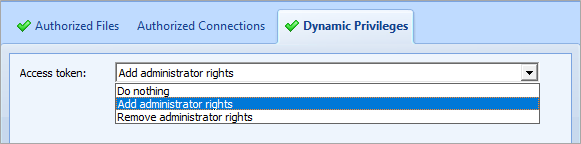 Figure 1: Administrators can add
Figure 1: Administrators can add Administrator rights to applications
Details
Workspace Control runs a service named Ivanti Workspace Control PE that exposes a Named Pipe. Normally only Composer (pfwsmgr.exe) is allowed to connect to this Named Pipe and send commands to the service. It is possible for a local attacker to bypass this restriction by spawning a new Composer process, inject a new thread in this process, and connect to this Named Pipe.
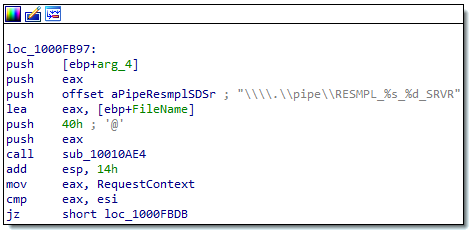 Figure 2: Named Pipe created by the Ivanti Workspace Control PE service
Figure 2: Named Pipe created by the Ivanti Workspace Control PE service
When connected to the Named Pipe it is possible to write a command to the Named Pipe, which starts an application that will be executed with elevated (Administrator) privileges. Methods for communicating with the Named Pipe are exposed in the ResMpc.dll file. Composer uses this DLL, however these methods can also be leveraged by the attacker to exploit this issue.
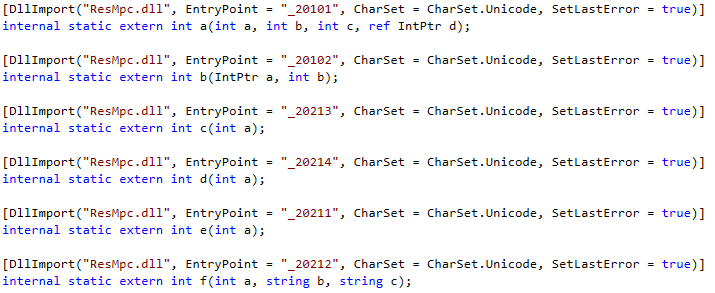 Figure 3: Composer uses the methods exported in ResMpc.dll for communicating with the Named Pipe
Figure 3: Composer uses the methods exported in ResMpc.dll for communicating with the Named Pipe
A local attacker can use this issue to run an arbitrary command with elevated privileges and fully compromise the workstation. If application whitelisting is enabled, an attacker first needs to find a way to run arbitrary code (eg, through a macro).