Abstract
Ivanti Workspace Control contains a flaw where it is possible to access folders that should be protected by Data Security. A local attacker can bypass these restrictions using localhost UNC paths. Depending on the NTFS permissions it may be possible for local users to access files and folders that should be protected using Data Protection.
See also
CVE-2018-15590 DOC-69682 - Ivanti Workspace Control Files and Folders Security has been improved
Tested versions
This issue was successfully verified on Ivanti Workspace Control version 10.2.700.1 & 10.2.950.0.
Fix
This issue was resolved in Ivanti Workspace Control version 10.3.0.0.
Introduction
Ivanti Workspace Control (formerly known as RES ONE Workspace) is a User Environment Management solution. The Data Security feature can be used to restrict access to certain files and folders on the local machine (regardless of their NTFS permissions). Data Security is essentially a path blacklist. It was found that it is possible to bypass this blacklist and access protect folders.
Details
On Windows it is possible for low privileged users to address local files via a localhost UNC path. Data Security does not take this into account, thus allowing local users to bypass Data Security folder restrictions using localhost UNC paths. In the following example access to the C:\Secret folder is protected using Data Security.
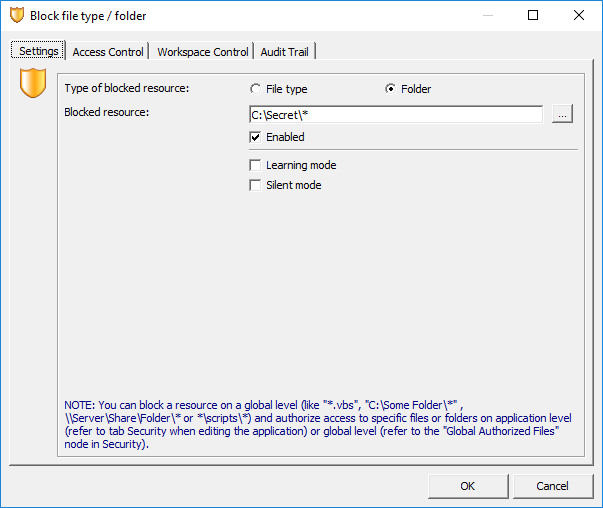 Figure 1: Data Protection is configured for
Figure 1: Data Protection is configured for C:\secret
Despite this configuration the folder is still accessible through the \\localhost\c$\secret UNC path. Depending on the NTFS permissions it may be possible for local users to access files and folders that should be protected using Data Protection.
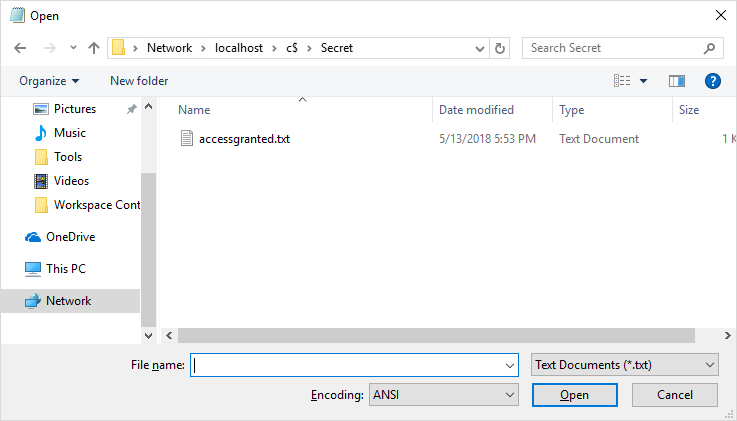 Figure 2: UNC path gives access to the protected folder
Figure 2: UNC path gives access to the protected folder