Abstract
VTech's DigiGo is a hand held smart device for children. The web browser included in the DigiGo does not validate TLS certificates when creating secure connections, allowing man in the middle attacks on web traffic.
Tested versions
This issue was tested on a VTech DigiGo running firmware version 83.60630. It is likely that other versions are also affected.
Fix
VTech pushed a firmware update to address this issue on 30 November, 2017. The firmware version still displays as 83.60630.
Introduction
VTech's DigiGo is a hand held smart device for children. The device contains multiple apps, including a browser. The browser does not validate TLS certificates when creating secure connections. An attacker that can perform a man in the middle attack can read and manipulate web traffic.
Details
The internet browser of the DigiGo is designed for kids. Only whitelisted domains are allowed to be visited. The device contains an initial list of domains. The list can be expanded by parents via a Parental Control interface. All traffic created from a whitelisted domain is allowed, such as including content from domains that are not whitelisted.
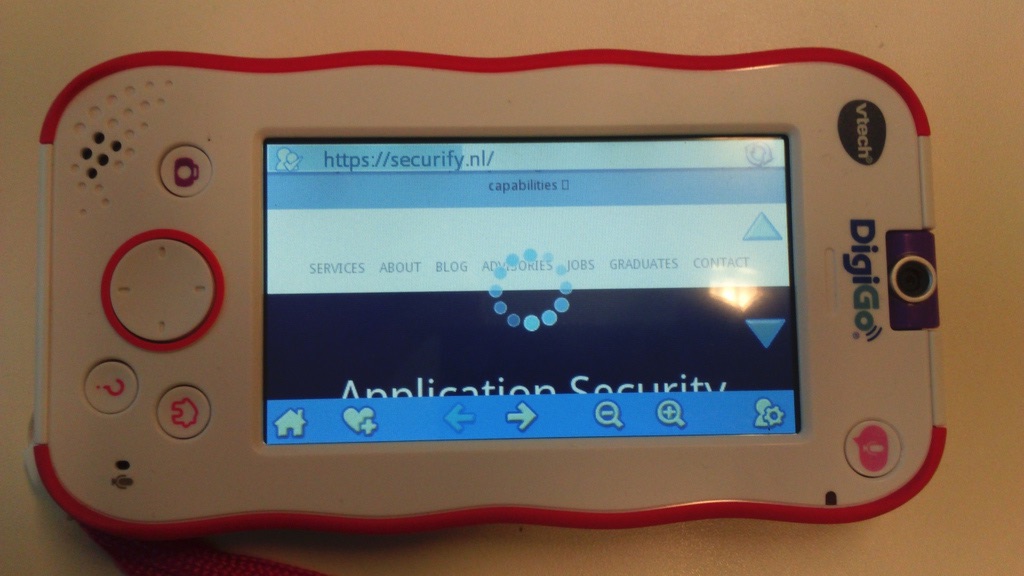
TLS certificates are not validated for any connection. This allows attackers that can perform a man in the middle attack to hijack all browser traffic.
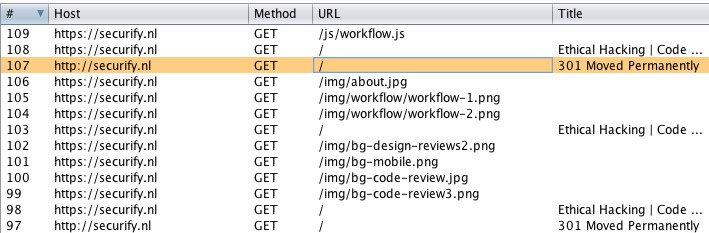
The Parental Control interface only allows adding (insecure) HTTP URLs. It's not possible to add URLs starting with https://.. However, the whitelist works on a per-domain basis. After entering the HTTP URL, the device extracts the domain from the URL, and allows any traffic from that domain. This means that the device will always connect to an insecure URL first. HSTS is ignored. So it’s always possible to hijack the connection on the first request, even if TLS certificate validation would be implemented.
The following two screenshots show the DigiGo visiting securify.nl. Burp's TLS certificate is not validated. Also, the first request is always done without TLS, ignoring HSTS.