Abstract
Multiple Cross-Site Scripting vulnerabilities were found in Synology Download Station. These issues allow attackers to perform a wide variety of actions, such as stealing victims' session tokens or login credentials if available, performing arbitrary actions on their behalf but also performing arbitrary redirects to potential malicious websites.
Tested version
These issues have been tested on Synology Download Station version 3.5-2956 and version 3.5-2962.
Fix
Synology reports that these issue have been resolved in:
- Download Station version 3.5-2962 [Create download task via file upload]
- Download Station version 3.5-2967 [Create download task via URL]
Introduction

Download Station is a popular Synology web application with more than 6.879.000 installations. Synology Download Station users can download files from multiple file hosting sites like BT, FTP, HTTP, NZB, Thunder, eMule, and more. Download Station is generally used by users that use their NAS as an entertainment hub, residing within the user's home network. Most users do not realize that these NAS devices are an entry point for attackers into their home network.
Multiple Cross-Site Scripting vulnerabilities were found in Synology Download Station. These issues allow attackers to perform a wide variety of actions, such as stealing victims' session tokens or login credentials if available, performing arbitrary actions on their behalf but also performing arbitrary redirects to potential malicious websites.
Persistent Cross-Site Scripting in "Create download task via file upload"
Users can create download tasks by uploading files (.torrent, .NZB or .txt) to Download Station. The "Create download task via file upload" feature is vulnerable to persistent Cross-Site Scripting. An attacker can create a specially crafted Torrent file containing a Cross-Site Scripting payload via the 'name' parameter. If a victim uses the "Create download task via file upload" feature to import file in Download Station, the payload will be executed within the browser context of the (authenticated) victim.
The following video shows how a Torrent file can be used to load an arbitrary website in an iframe.
Persistent Cross-Site Scripting in "Create download task via URL"
Users can create download tasks by manually entering URLs or searching for Torrent files with BT Search. The "Create download task via URL" feature is vulnerable to persistent Cross-Site Scripting. An victim can unknowingly download a malicious Torrent file through BT Search containing an Cross-Site Scripting payload in the download site URL.
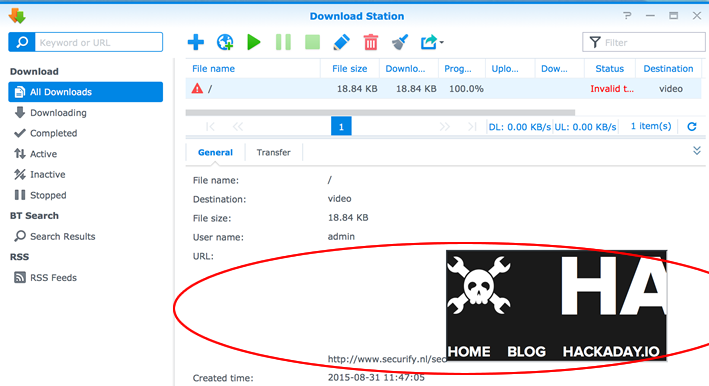
Proof of concept
GET /webman/3rdparty/DownloadStation/dlm/downloadman.cgi?urls=%5B%22http%3A%2F%2Fwww.securify.nl%2Fsec**%3Ciframe%20src%3D'http%3A%2F%2Fwww.hackaday.com'%2F%3E**.torrent%22%5D&action=add_url_task&desttext=video&file_info=on HTTP/1.1
Host: 192.168.1.14:5000
User-Agent: Mozilla/5.0
*X-SYNO-TOKEN: l1ekJnPhUXm5o*
Cookie: stay_login=0; id=l1GnmfyQR60ms13A0LTN001710
Connection: keep-alive
Pragma: no-cache
Cache-Control: no-cache
It should be noted that the X-SYNO-TOKEN header provides protection against Cross-Site Request Forgery attacks. As of DSM version 5.2-5592 Update 3, this protection is enabled by default. In addition the DS Video app requests do not include this Cross-Site Request Forgery protection.