Abstract
Virtuozzo Power Panel is a solution that allows customers of service providers to manage their virtual environments. Virtuozzo Automator is an administrative tool for managing the service provider's virtual infrastructure. Both products are affected by a buffer over-read vulnerability that allows attackers to read random server memory.
Tested versions
This issue was tested on Virtuozzo Power Panel version 6.1.2.
Fix
A fix for this issue is included in the following software versions:
- Virtuozzo Power Panel 6.1.2-hotfix5
- Virtuozzo Automator 6.1.2-hotfix5 and 7.0.2-hotfix1
Introduction
Virtuozzo Power Panel and Automator include a file manager. The file manager can be used to read files from a virtual environment. By changing parameters in the request to retrieve a file, it's possible to retrieve random server memory. This vulnerability allows an attacker to retrieve confidential information, such as cookies from other users.
Details
Virtuozzo Power Panel and Automator include a file manager. The file manager can be used to read files from a virtual environment. When requesting a file, a URL in the following format is called:
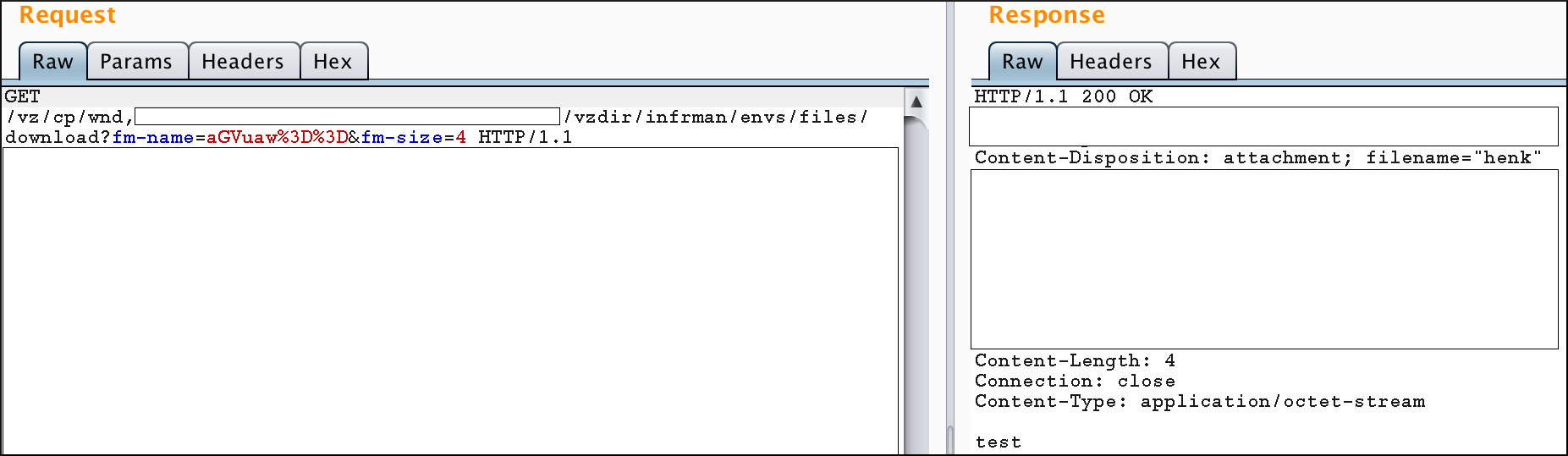
vzdir/infrman/envs/files/download?fm-name=<base64 encoded filename>&fm-size=<size of the file>
The image below shows a user downloading the file henk with content test (size = 4).
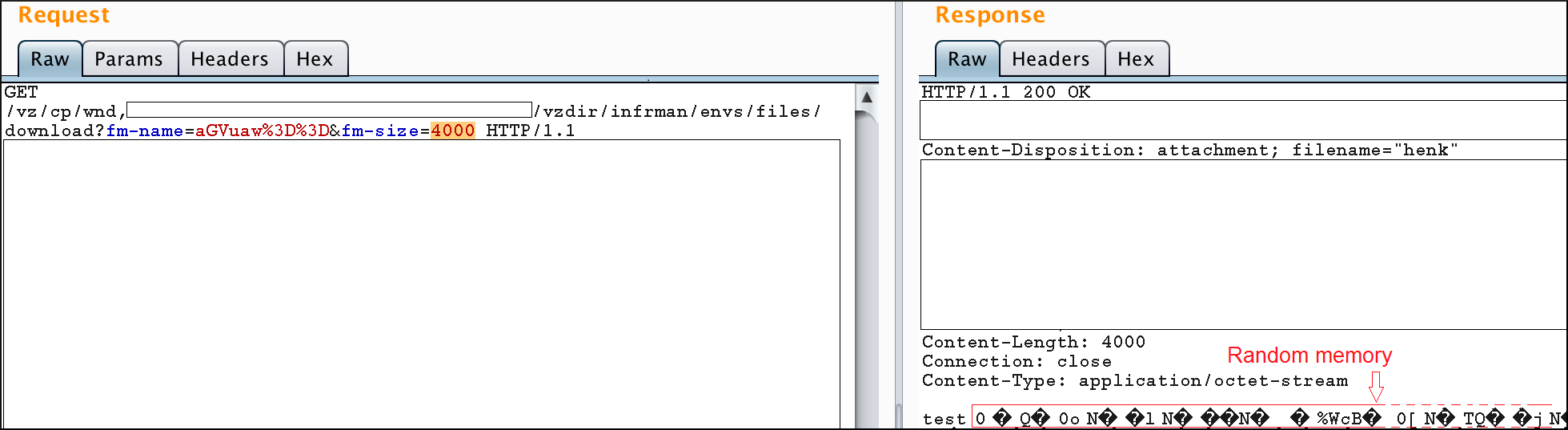
By manipulating the size parameter, it's possible to trigger a buffer over-read that will cause the httpd worker to leak memory. An attacker can use this to make dumps of memory and retrieve confidential information.
According to Virtuozzo the following software versions are affected by this issue:
- Virtuozzo Power Panel version 6.0.0 through 6.1.2-hf4
- Virtuozzo Automator version 6.0.0 through 6.1.2-hf4 and version 7.0.0 through 7.0.2
Timeline
- 20 May 2017: Discovered vulnerability.
- 22 May 2017: Reported to Virtuozzo.
- 23 May 2017: Virtuozzo replied and started to create a patch. During preparation of fixes for the vulnerability, Virtuozzo found the same file manager component in the Virtuozzo Automator admin panel.
- 06 June 2017: Hotfixes published.
Response from Virtuozzo
I would like to thank Virtuozzo for their quick response and proper fix for the vulnerability. They provide a detailed description of the impact. The vulnerability was initially discovered in the Virtuozzo Power Panel. During preparations for the fix, Virtuozzo found the same file manager component in the Virtuozzo Automator admin panel and fixed both.
The following paragraphs show the detailed description received from Virtuozzo about the impact of the vulnerability.
"During preparation of fixes for the vulnerability, we've found that the same "file manager" component is also used in the Virtuozzo Automator admin panel. This panel is used only by the infrastructure administrators of the hosting provider, while Virtuozzo Power Panel is a management panel for the end users. These two panels are always hosted in different environments (Containers/VMs), i.e. VA installer wouldn't allow to setup them in the same environment. Thus, administrator's credentials wouldn't be intermixed with end-users credentials in case an attacker dumps all memory of the httpd process, which serves VZPP."
"There is one instance of Power Panel per hardware node. It runs on the host. By default, the panel is hosted by an Apache httpd configured with prefork workers. A Power Panel User accesses a VZPP instance by connecting to his virtual environment's (CT/VM) address (IP/domain) and a custom port (6443 by default) (see the user's guide for details). Software on the node routes the request to user's environment_address:6443 to this particular node's VZPP instance. Thus, all users, that have CTs/VMs on this hardware node, effectively share one instance of VZPP, served by multiple httpd workers. In the worst case, an attacker may gain access to cookies/session info of other users, that are also hosted on the same hardware node and have recently accessed their CTs/VMs via VZPP and their requests were served by the same httpd worker."