Abstract
A security vulnerability was found in Kaseya VSA file upload file functionality. Using this vulnerability an authenticated user in a Kaseya VSA environment is able to upload arbitrary files onto the server. This functionality can lead to remote code execution with an asp shell.
Tested versions
This issue was successfully tested on version 9.2
Fix
Patch to the latest version of VSA.
Introduction
Kaseya VSA allows a company to manage computers deployed all over the world from a central interface, sometimes hosted in their own environment, and other times as a SAAS. This system is designed to centralise IT automation including patch management, inventory management, remote monitoring, remote access and more. Some of the functionality of this management backend includes:
- Ability to take a screenshot on the remote computer
- Ability to download files form remote computer
- Ability to upload files to remote computer
- Ability to reboot / shutdown remote computer
This issue was found in the ability to upload files to the remote computer functionality.
Details
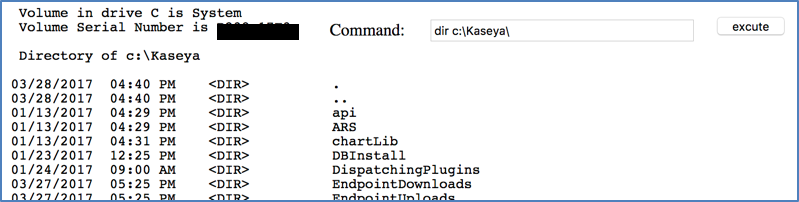
An authenticated user is able to upload a file to the remote computer. This is done via uploading to a folder on the server, then the server sends it to the remote computer. The server is vulnerable to uploading arbitrary files, inducing custom ASP or ASPX script and executing it from the upload directory as there is no protection around file types uploaded, or ability to read from the upload directory.
Steps to reproduce
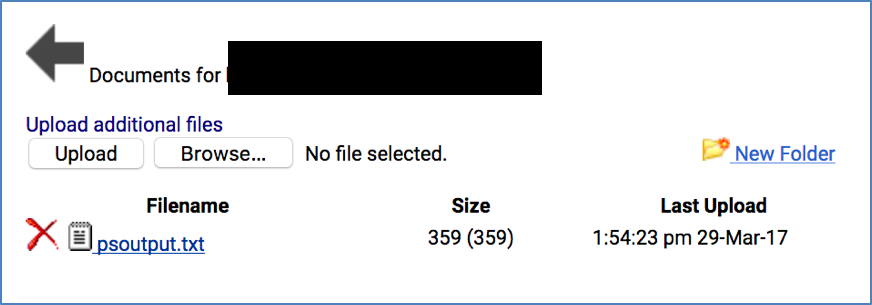
- Go to the file manager or “Documents” of a machine:
- Upload an ASPX shell:
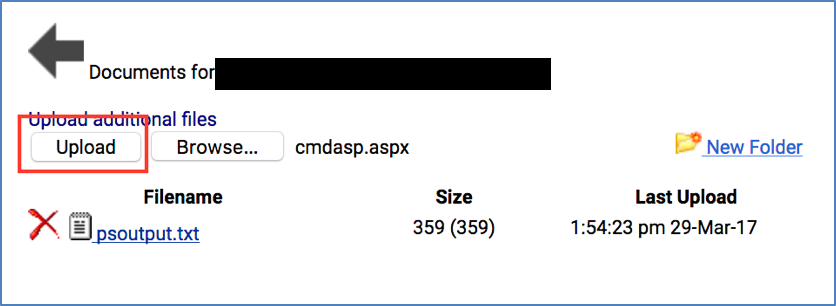
- Example shell: cmdasp.aspx — cmd.aspx is a basic asp command shell
- Open the script in a new tab:
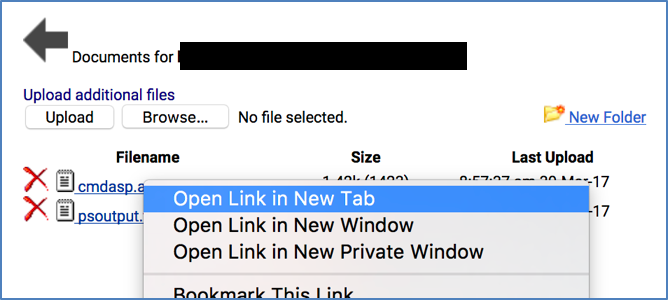
- Code execution