Part 1: what is attack modeling?
While performing security assessments, we at Securify noticed that even though frameworks and network appliances are becoming more secure. Applications and appliances more often than not, provide secure default values regarding the configurations. In addition, we see that guidelines such as those provided by the NCSC are implemented far more often. This was not always the case and shows an increase in security knowledge. At Securify we however aim not only to discover vulnerabilities of a technical nature on just a single system or application, but also try to cover advanced organization wide risks by analyzing your organization’s landscape and all relevant components included.
This however enlarges the scope of the attack model which will result in a lot of risks that need to be validated, managed and tested. This will cost a lot of money and effort and might initially not be worth the resources invested. This where attack modelling proves it’s value. By further analyzing the company wide risks a path with the least resistance can be determined to the most sensitive assets within the organization’s landscape. This will result in a roadmap ordered by risk to increase the resilience of an organization, one scenario at a time.
Attack modeling vs. threat modeling
Attack Modeling is creating a list of possible concerns together with all parties involved from the perspective of an attacker. By creating an attack model, a real-world attack scenario can be simulated which can quickly give you an initial insight into your organizations attack surface. Attack modeling is a derived form of threat modeling, which we use at Securify to better aid customers in obtaining a grip on their organization wide risks and make them more cyber resilient.
To fully understand attack modeling and how it differs from threat Modeling, it is necessary to distinguish these terms from one another. A threat model is a collection of all possible threats, and a threat is a possible risk to an application, network or organization. Once the threat is recognized, further research needs to be performed to gain a better understanding of the threat in question. Normally during this phase, the threat modeler will start to incorporate the impact and likelihood into the model to prove the importance of the threat. Once a consensus is reached together with the stakeholders, the threat will establish itself as a risk that can be managed. While discussing threats to obtain consensus, it’s important to keep in mind that if you cannot think of a certain impact to accompany your threat, is it still a valid threat?
It's all about the crown jewels!
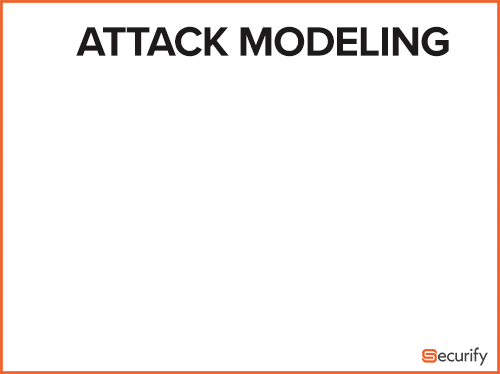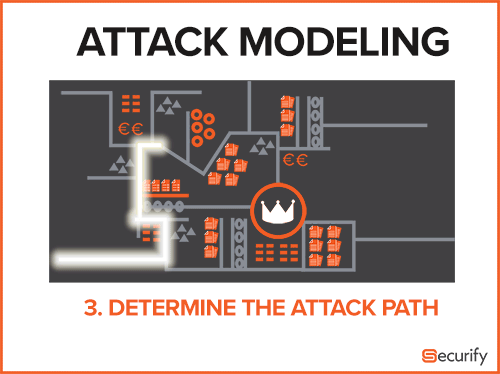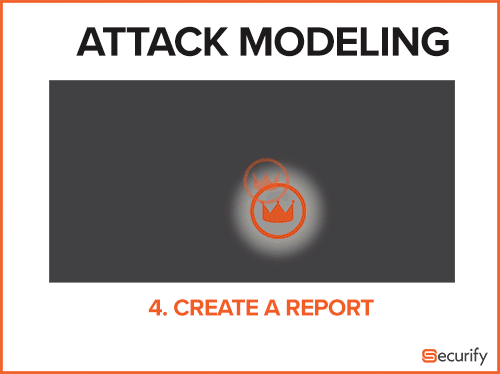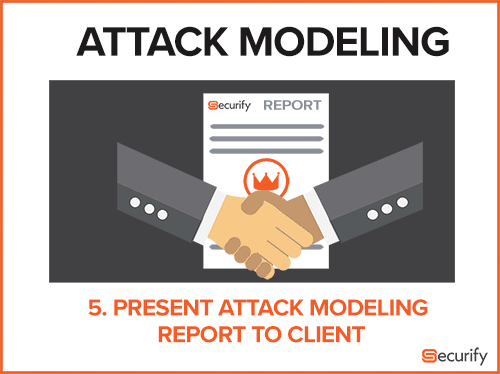
Attack modeling takes a different approach. By trying to determine the biggest risk of the customer by identifying where the most sensitive target resides, this is what offensive security specialists like to define as the ‘crown jewels’. This can be a database server on a network, a file on disk or even a four-eyed principle employed in a process to ensure the integrity of a sensitive operation. Based on the location of the most sensitive target or action, the parts an attacker can influence will be traced throughout the targeted landscape to determine all personnel and processes involved, resulting in the attack path that has the highest likelihood of succeeding. A general rule of thumb while attack modeling is that if there is no data obtain or process that can be influenced, there is theoretically no possible attack path to the crown jewels.
Attacking and defending
Attack Modeling puts the emphasis on ‘attack’ by detecting sensitive actions, discovering the crown jewels and using that information to create an attack path. This path can be exploited by leveraging vulnerabilities that are usually of some technical nature, but for example can also be of physical nature. Threat Modeling should be done in advance to aid organizations, developers and administrators in obtaining a better grip on their risks. Additionally, this will force all parties involved to think about all possible threats and to relay this information to all parties involved in the form of a model during the development stage of a project.
After reading this blog post it should be clear what the differences are between threat modeling and attack modeling. From a high overview they can seem one and the same but focus on different sides of the same coin (Attacking vs. Defending) and result in different deliverables with both try to achieve a different goal.
If you enjoyed this article and want to stay up-to-date with our latest posts on cybersecurity and penetration testing, be sure to follow us on LinkedIn. Securify regularly publishes new content on various topics, including best practices, tools and techniques, and industry trends. Securify also offers a range of penetration tests and continuous support for improving companies' security posture to help them stay at the top of their game.