Red teaming
Simulate real attacks
What is Red Teaming?
Red Teaming is an exercise in which an organization is attacked by ethical hackers. The group of hackers carrying out the attack is called the Red Team.

Test your greatest fear
Are you unsure whether your organization can stop a major cyber attack on your organization and operation?
Stage a real attack
We attack your organisation, while you try to defend.
Measure your capabilities
Evaluate your detection & response capabilities.
Increase your resilience
Learn from a specific scenario to minimize real damage from a real attack.
Our team
We stage a planned (cyber) attack on your organisation while recording every step.
Your team
You try to detect & mitigate the incoming attack.

Red Teaming: A serious game
So you think your code, product and infrastructure are rock solid? Now it is time to test how your organization, your people and your processes deal with a real cyber threat.
Red Teaming is the ultimate test for organizations that have already developed a base maturity level in their security. By measuring how you react to a real attack, you can further ramp up your resilience and base your security investments on real insights and numbers instead of gut feeling and assumptions.

Meet your opponent
Our multidisciplinary team of seasoned and highly motivated professionals will stretch you to your limits to detect and mitigate the incoming attack.
Our typical team looks like this:
- Red team lead
- Sociaal engineering expert
- Windows and Active Directory guru
- Monitoring specialist
- Malware-expert

Your Blue Team
The specialists in the Blue Team form the defence. This team is all about detection and prevention. It is their day job to ensure that the IT environment is secure. That someone without rights cannot get into systems and hackers cannot steal data or money. The goal is to neutralize all threats as quickly as possible.
The security guards also have all kinds of systems and methods at their disposal. Think of MFA, email filters, a SOC (Security Operations Center), SIEM (Security Information and Event Management), patch management and so on.
Your red teaming options.
ART
Een Red Teaming test volgens het Advanced Red Teaming framework van DNB.TIBER
A Red Teaming test according to the TIBER-NL/EU Framework of DNB
ZORRO
A Red Teaming test according to the ZORRO framework of Z-CERTDORA - TLPT
Threat Lead Penetration Testing

Fair play
Winning the Red Teaming exercise is not our goal. We want to provide you with as many actionable insights as possible. Immediately after starting the attack, we keep you up to date and support you in your decision-making process.
The best lessons are learned when you operate just outside your comfort zone. Once we notice that you can successfully prevent, detect and respond to basic attacks, we slowly ramp up our sophistication level and stretch you to your limits.
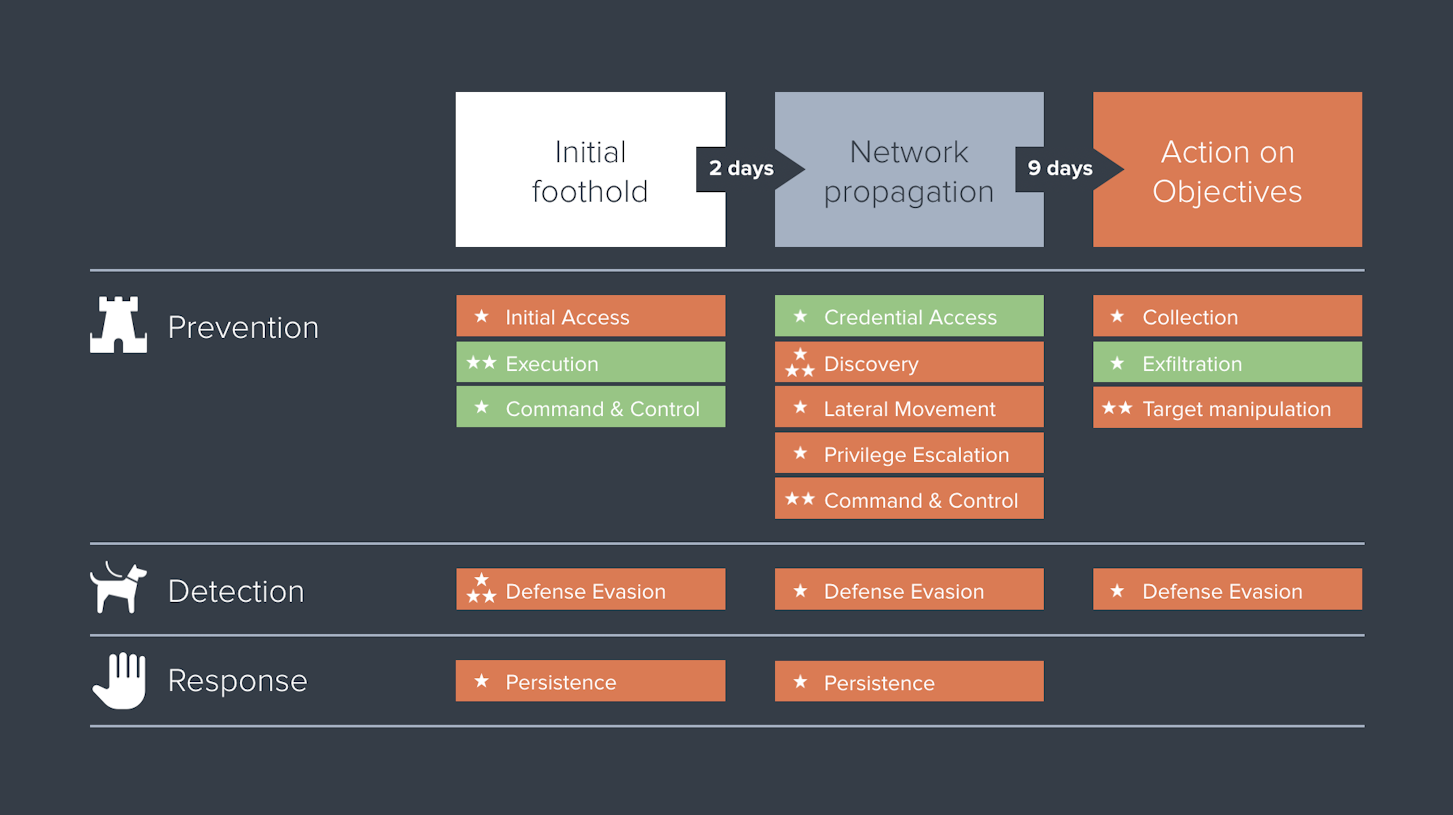
We ♥ Metrics
Our Red Teaming approach is based on the Unified Kill Chain (UKC), a science-driven real-world attack model that goes beyond the initial foothold phase and also takes network propagation and action on objectives into account.
By combining UKC metrics with the Mitre ATT&CK framework, we can generate a powerful number-driven overview of how your organisation has performed during the Red Teaming exercise.
The Red Teaming process
A Red Team Test always proceeds according to a preconceived plan. The scope, duration and purpose of the test is determined in consultation with the client.
The exploration
This is followed by the reconnaissance phase, in which the red team collects as much information as possible about the organization, the existing systems and the target of the attack. For example the crown jewels. The scenario is also created during this phase. The choice of scenario depends on how mature the IT security of the organization is. And whether an organization wants to know whether they can withstand a certain TA, where they will recreate the path of a certain TA.
The Red Teaming Test
This is followed by the Initial Foothold with which access to a system, a workplace or a user account is obtained. Once inside, the Red Team tries to extend control by increasing user permissions. They also try to achieve remote control over internal resources in the network. Then the search for the most valuable assets of the organization starts. Consider, for example, access to the payment system. This is the Trophy Hunt.
After the Red Teaming Test
After the test, the client is presented in a findings meeting what the Red Team has done and how far they have come. An extensive report also contains recommendations and advice for improving security. If desired, an advisory process can be started. In an advisory process, our security specialists help to solve the identified issues.