Abstract
File Roller (Archive Manager) is affected by a path traversal vulnerability. It is possible to create a specially crafted archive file that once extracted will cause malicious files to be created in arbitrary locations.
Affected versions
This issue affects File Roller 3.6.0 up to 3.6.4, 3.8.0 up to 3.8.3 & 3.9.1 up to 3.9.3.
It was successfully verified on the following Linux distributions:
- Ubuntu 12.10 with File Roller 3.6.1.1 installed
- Ubuntu 13.04 with File Roller 3.6.3 installed
- Fedora 18 with File Roller 3.3.6 installed
See also
- 2013-001: File Roller path sanitization errors
- CVE-2013-4668
- USN-1906-1 File Roller vulnerability
Fix
The maintainer of File Roller released a patch that fixes this issue: https://git.gnome.org/browse/file-roller/commit/?id=b147281293a8307808475e102a14857055f81631
This issue is fixed in the following versions of File Roller:
-
File Roller 3.6.4: http://ftp.gnome.org/pub/gnome/sources/file-roller/3.6/file-roller-3.6.4.tar.xz http://ftp.gnome.org/pub/gnome/sources/file-roller/3.6/file-roller-3.6.4.sha256sum
-
File Roller 3.8.3: http://ftp.gnome.org/pub/gnome/sources/file-roller/3.8/file-roller-3.8.3.tar.xz http://ftp.gnome.org/pub/gnome/sources/file-roller/3.8/file-roller-3.8.3.sha256sum
-
File Roller 3.9.3: http://ftp.gnome.org/pub/gnome/sources/file-roller/3.9/file-roller-3.9.3.tar.xz http://ftp.gnome.org/pub/gnome/sources/file-roller/3.9/file-roller-3.9.3.sha256sum
Introduction
File Roller (also known as Archive Manager) is an archive manager for the GNOME desktop environment. It supports various archive types like Zip, 7z & tar.
Path traversal
It has been discovered that File Roller does not handle certain archive files in a secure manner. It is possible to create a specially crafted archive that once extracted will cause malicious controlled files to be created in arbitrary locations. It should be noted that File Roller will not silently overwrite existing file. Consequently, an attack is limited to creating new files.
If the target file already exists, File Roller will display a dialog asking the user what to do. In case the Extract Here option from the Context Menu is used, File Roller will (silently) ignore any existing file.
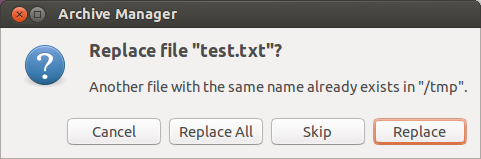 Figure 1: replace file dialog
Figure 1: replace file dialog
Proof of concept
The following script can be used to verify this issue.
#!/usr/bin/env python
import sys, tarfile
def main(argv=sys.argv):
tf = tarfile.open("test.tar", "w")
tf.add("/etc/issue", "test/../../../../../../../../../../../tmp/test.txt")
tf.close()
return
if __name__ == '__main__':
main()