Introduction
In a previous blogpost, I've written how to combine Gnirehtet & proxychains in order to intercept traffic from mobile apps over adb while on a VPN. After some time, the setup seemed to be somewhat buggy and slow. A contact of @FSDominguez suggested to look into port forwarding. I'd like to present a revised adb reverse tethering MITM setup.
adb reverse
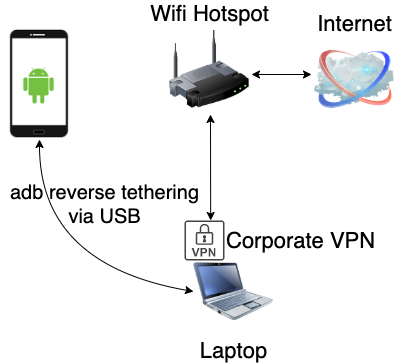
The Android Debug Bridge (ADB) command-line tool provides several utilities such as performing shell commands on the device, (un)installing apps, pushing/pulling files and port forwarding. Speaking of port forwarding, there's a nifty yet relatively less known command adb reverse which essentially allows us to create a reverse proxy by forwarding requests on a port on the mobile device to a port available on the host.
A quick hands-on example:
adb reverse tcp:4444 tcp:8888
echo "hello world" > index.php
php -S 127.0.0.1:8888
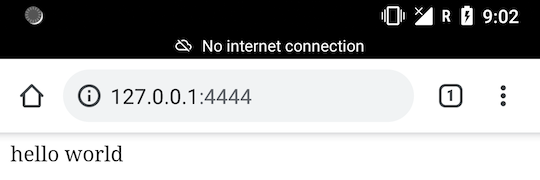
The last command launches a PHP web server listening on port 8888 (localhost). Opening 127.0.0.1:4444 in a web browser on the mobile device gives us:
Installation steps of the revised setup
Since Android is based on Linux, it is possible to use iptables in combination with adb reverse in order to forward all traffic from mobile apps to the host device. Note that this requires root access and a transparent intercepting proxy.
-
Install an intercepting HTTP proxy, configure it to listen on incoming connections and make sure to enable "transparent proxy"; Example:
127.0.0.1:8844. In Burp Suite, go to Proxy > Options > Edit or add a proxy > Request handling > check "Support invisible proxying".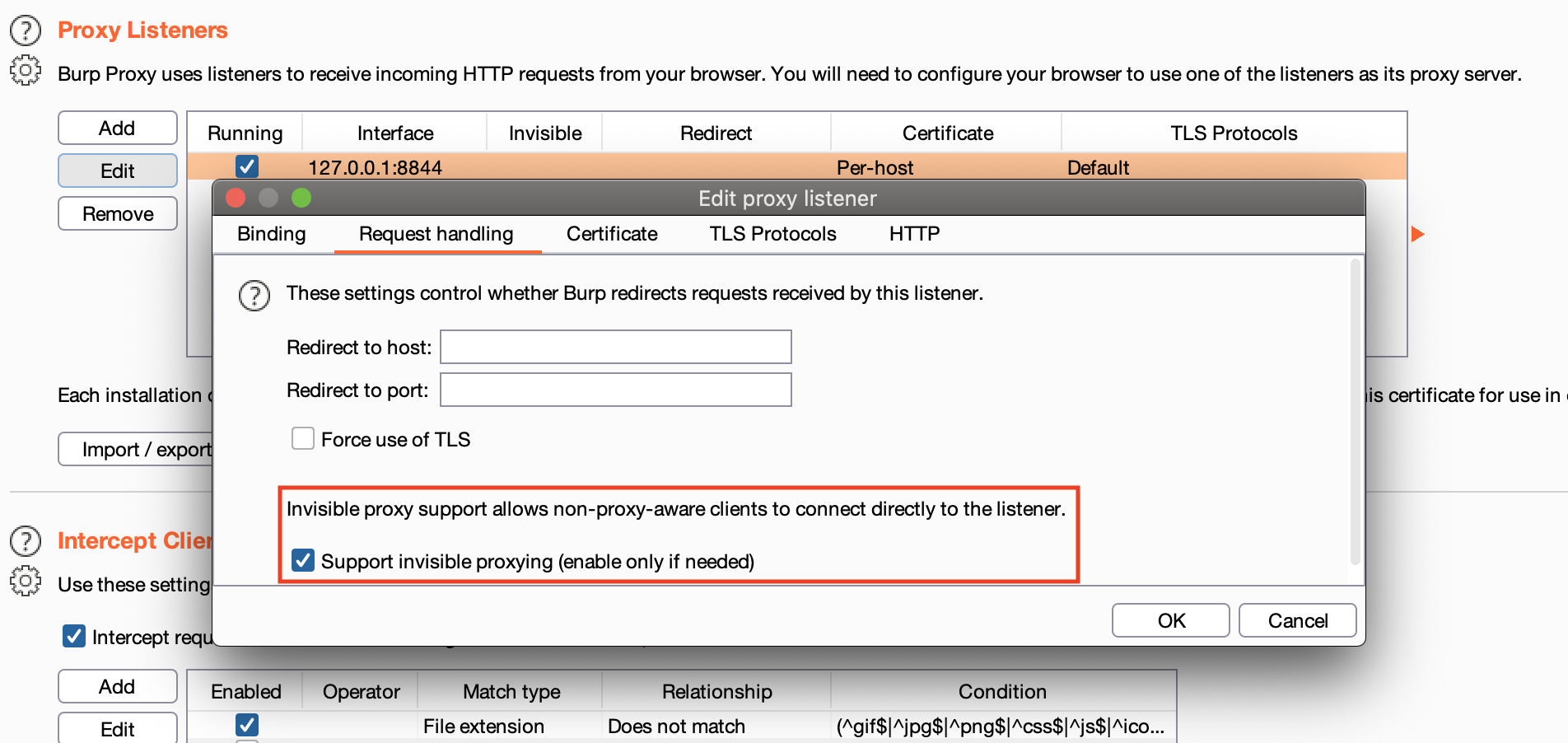
-
Connect your phone to your host using a USB cable.
-
Perform the following command on your host:
adb reverse tcp:8844 tcp:8844 -
Connect your mobile device to any WiFi network.
-
Next we need to perform administrative commands on the device:
adb shell # to perform commands on the device
su # switch to root
iptables -t nat -F # flush current rules
# forward traffic from port 80 & 443 to 8844
iptables -t nat -A OUTPUT -p tcp --dport 80 -j DNAT --to-destination 127.0.0.1:8844
iptables -t nat -A OUTPUT -p tcp --dport 443 -j DNAT --to-destination 127.0.0.1:8844
iptables -t nat -A POSTROUTING -p tcp --dport 80 -j MASQUERADE
iptables -t nat -A POSTROUTING -p tcp --dport 443 -j MASQUERADE
⚠️ if you suspect that your target app performs requests on other ports than 80 and 443, adjust above commands accordingly.
- In order to see HTTPS traffic in your intercepting proxy, you will need to install a CA certificate on the Android device. Checkout some of NVISO's blogposts 1 & 2 and of course the manual of your favorite intercepting proxy.
- To reset and restore your setup:
adb reverse --remove-all
adb shell
su
iptables -t nat -F
Automation
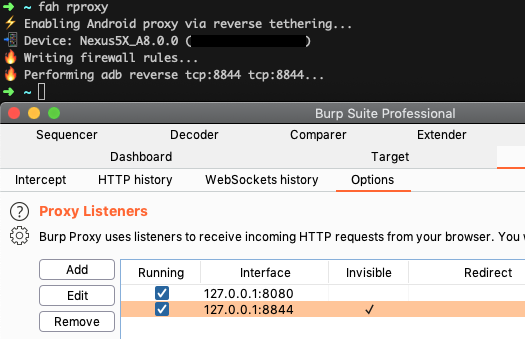
I've automated above setup and commands in my Frida Android Helper tool. Just run fah rproxy and you're good to go!